
Keeping data secure: playing it safe online is a team effort
Keeping sensitive data and systems safe is crucial for businesses seeking to survive and thrive online – including the accommodation industry. Whilst Seekom’s suite of security solutions provide top-of-the-line security, it’s key to know that online security is a team effort as a chain is only as strong as its weakest link.
In this article, we explore the different ways Seekom's cloud-based solution keeps users secure and how you can play your part in reducing the risk of cyber threats.

Password protection is paramount
The first step to playing it safe with data protection is the padlock on the online door, also known as a password.
Passwords can be fun; make them quirky, not “qwerty”, to be memorable. Incorporating a compliment to remind yourself of one of your positive qualities, or using a short joke to bring on a smile at every log in is a great way to do this. Passphrases can be a lot easier to remember than just passwords and are stronger due to their complexity.
Strong passwords are long and wrong – avoid normal spelling of words by substituting capital letters, numbers and punctuation marks and use at least eight characters to beef up that padlock.
Passwords shouldn’t include any personal or business information that might easily be guessed, such as “Hurricanesfan”.
A common password faux pas is to use the same password across different platforms, allowing one password compromise to lead to many.

Bespoke authority levels offer you more control
Seekom’s property management platform allows users to set bespoke authority levels for different staff members, ensuring staff have only got the access they require to get their job done. As well as avoiding any unpleasant surprises, this helps users ensure they are complying with best practise.
Bespoke authority levels reduce the likelihood of staff sharing login details, which is best avoided, and means that access for particular individuals can easily be revoked when necessary, for example when staff members leave.
It may be a good time to double check staff access levels and be aware, for example, of exactly which staff have administration access to amend a property's bank account details on guest invoices.
We recognise you may prefer to grant different levels of access to Seekom iBex for different roles and staff within your business. That’s why our software puts the power in your hands when it comes to controlling who can do what within your business.
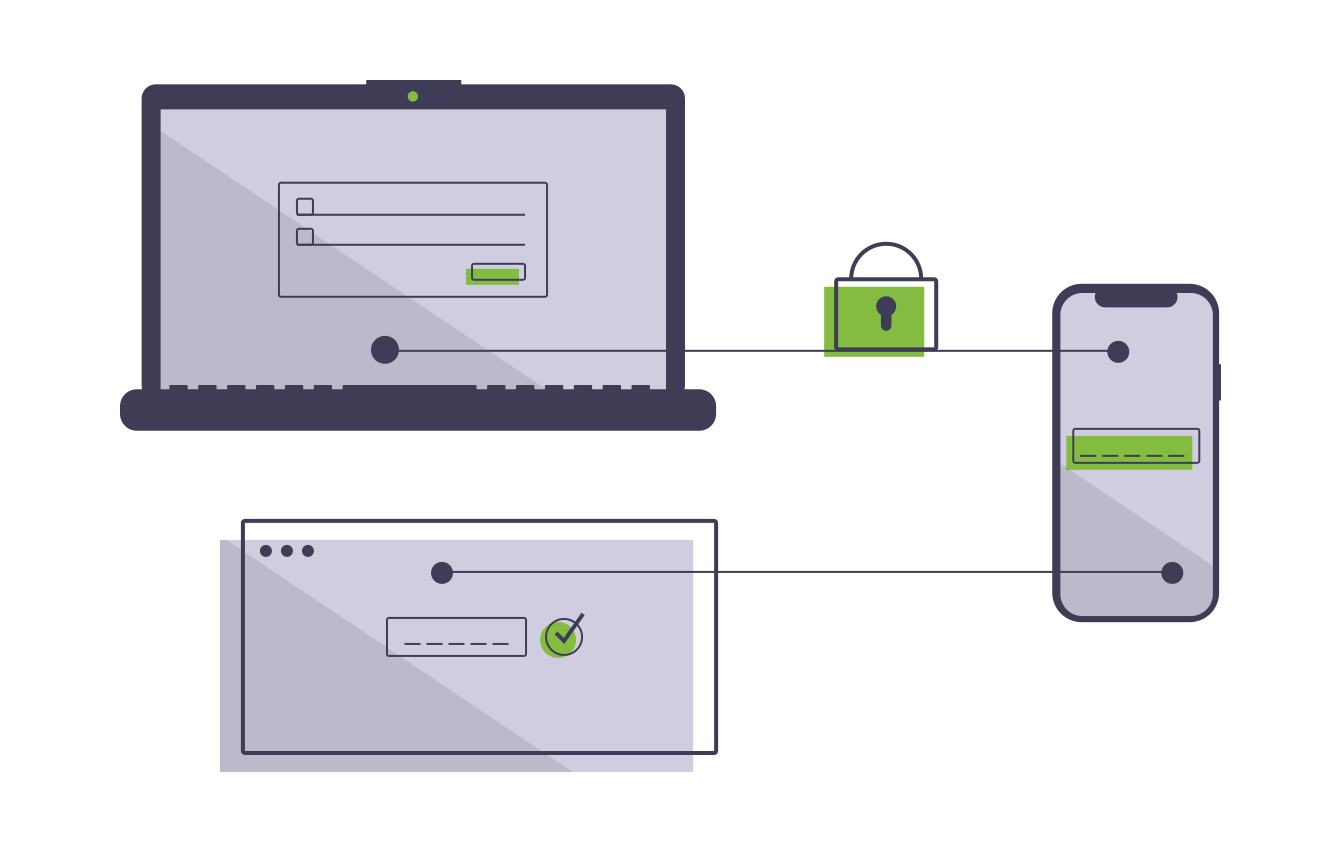
Multi-factor authentication adds security
Multi-factor authentication is like a bouncer at a nightclub checking punters’ IDs to make sure that they are who they say they are and that everything adds up.
The way it typically works is by sending a message to a mobile phone when a password is entered, double-checking that anyone seeking access has the right password and the right phone.
The message provides a one-time code that must be provided to gain access, meaning that even if a hacker manages to obtain your password, they will not be able to gain access to your account.
The Seekom Vault has built-in multi-factor authentication that you can enable, due to the extra-high sensitivity of the information it contains.
If you are worried about one of your devices falling into the wrong hands and want to implement multi-factor authentication on your login screen or on any website or login screen that doesn’t currently have it setup, you can do so with a number of third party apps. For example, the Microsoft Authenticator app is available as a free download and allows you to add multi-factor authentication for individual websites. Apple’s operating systems offer the option to use multi-factor authentication on your initial login screen and for individual websites as well.
Seekom's got your back
Seekom provides premium protection to keep your data and systems safe. Behind the scenes we use extra layers of security as well as employing third party security specialists to run independent checks on our systems. We make it easy to comply with General Data Protection Regulation and Payment Card Industry requirements as part of our commitment to best practice.
These measures not only provide peace of mind to users but also demonstrate Seekom's commitment to security and our dedication to providing a safe and secure platform for our users.
One of our amazing business development managers will be in touch to showcase our product to you and talk you through how we can help grow your business.
Contact Us
PO Box 9300, Marion Square, Wellington 6141
Phone (NZ) : +64 4 974 9588
Phone (UK) : +44 20 3835 5939
Support: support@seekom.com
Websites: webhelp@seekom.com
Copyright 2022 © Seekom Limited (NZ owned)

